This article explores the USB keyboard protocol, explaining how keyboards communicate with computers via USB. We’ll start with USB hardware basics and protocol concepts, then dive into the Human Interface Device (HID) protocol to understand USB keyboard data exchange.
Prerequisite Knowledge: This article assumes a basic understanding of electrical signaling (including voltage levels), differential signaling and duplex communication.
Introduction to USB HID
The USB Port
The Universal Serial Bus (USB) was created in the mid-1990s to unify peripheral connections and simplify communication between devices and computers, replacing the cumbersome array of ports used before, such as serial and parallel ports.
To understand how the USB HID protocol operates, let’s first look at the physical structure of a typical USB connection, starting with the widely-used USB 2.0 standard.
USB 2.0 Port: Structure and Functionality
The USB 2.0 port is designed with simplicity and backward compatibility in mind. It uses a Type-A connector for host devices (such as computers) and Type-B or Mini/Micro USB for devices.
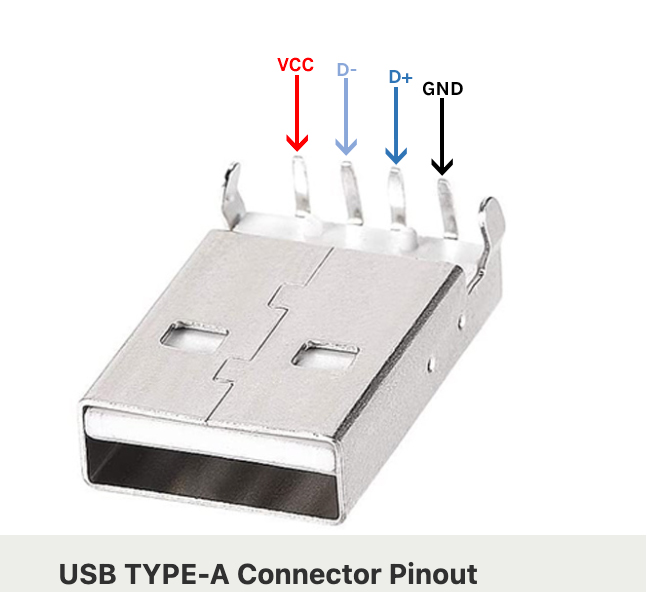
USB 2.0 Pinout (Type-A)
- Pin 1 (VCC): Provides a 5V power supply.
- Pin 2 (D-): Negative data line used for differential signaling.
- Pin 3 (D+): Positive data line used for differential signaling.
- Pin 4 (GND): Ground pin for completing the circuit.
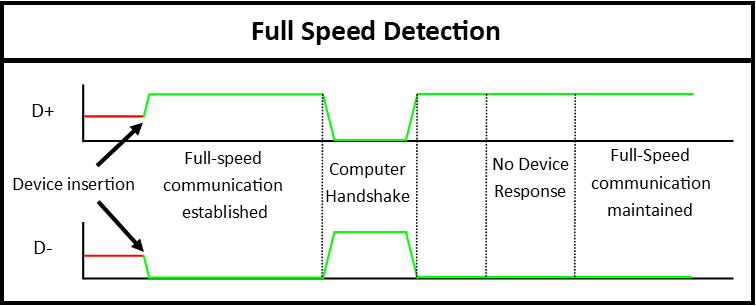
USB Speed Detection via D+ and D- Lines
When a USB device is connected, the host determines the communication speed based on the initial state of the D+ and D- lines. These lines are used for differential signaling, but their voltage levels during startup play a crucial role in speed detection:
- Low-Speed (1.5 Mbps): If D- is pulled to 3.3V while D+ remains grounded, the host recognizes the device as Low-Speed (used by devices like simple mice or basic keyboards).
- Full-Speed (12 Mbps): If D+ is pulled to 3.3V while D- remains grounded, the host identifies the device as operating in Full-Speed mode (used by most USB 2.0 devices, including many keyboards).
- High-Speed (480 Mbps): For USB 2.0 devices that can operate in High-Speed, the device first appears as Full-Speed (with D+ pulled up). The host then attempts to initiate high-speed communication through a special handshake procedure. If successful, both D+ and D- switch to differential signaling for the 480 Mbps speed.
This simple method of manipulating the voltages on the D+ and D- lines allows for seamless detection of the device’s capabilities without the need for additional hardware lines.

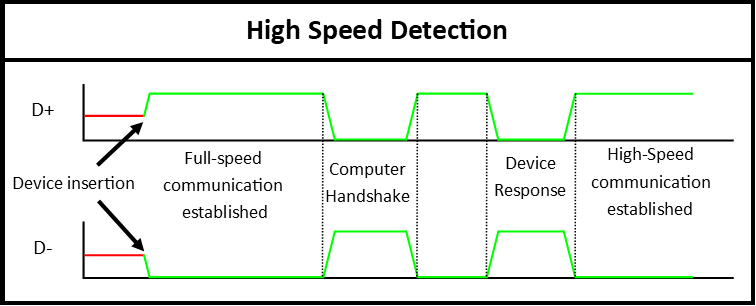
Example of a USB 2.0 Device Connecting at High-Speed:
Let’s say you plug in a USB flash drive (which supports High-Speed) into a USB 2.0 port on your computer.
-
Initial Detection: At first, the flash drive pulls D+ to 3.3V, signaling the host that it is a Full-Speed device. The host configures the communication to handle Full-Speed (12 Mbps).
-
Signal Handshake: The host then sends a signal pulse, alternating voltage states between D+ and D-, indicating it wants to switch to High-Speed.
-
Device Response: The flash drive recognizes the pulse and responds by sending its own signal pulses back to the host, confirming that it supports High-Speed.
-
Switch to High-Speed: After the exchange, the host and the flash drive both switch to High-Speed mode (480 Mbps). From this point onward, both D+ and D- operate in differential mode to send data at higher speeds.
Functionality
Data Transfer: The D- and D+ pins enable half-duplex communication with a maximum speed of 480 Mbps.
While USB 2.0 served as the dominant standard for a long time, its limited power and data transfer rates became a bottleneck for high-performance devices, leading to the development of USB 3.0.
Evolution of USB Port
As USB evolved, its core communication methods, such as differential signaling and duplex communication, remained intact, while the hardware and performance significantly improved.
USB 3.0 introduced major upgrades over USB 2.0:
- Speed: The most notable improvement is the jump to 5 Gbps with the SuperSpeed bus, which is 10 times faster than USB 2.0’s 480 Mbps.
- Power Delivery: USB 3.0 supplies 900mA of power, compared to USB 2.0’s 500mA, allowing for more demanding peripherals and faster charging.
- Full-Duplex Communication: Unlike USB 2.0’s half-duplex mode, USB 3.0 allows for simultaneous data sending and receiving, improving overall efficiency.
- Backward Compatibility: USB 3.0 retains compatibility with USB 2.0 devices, reverting to 2.0 speeds and power when necessary.
USB-C later refined the connector design with reversibility, higher data rates (up to 40 Gbps with USB4), and support for 100W power delivery (compared to 2.5W of USB 2.0), further broadening USB’s versatility.
USB Protocols Overview
The USB architecture supports multiple protocols that govern how devices communicate with a host. These protocols handle various data transfer needs, from high-speed mass storage devices to low-latency human interface devices.
Overview of different USB device classes
USB devices are grouped into classes, each defining a particular type of functionality. Some common classes include:
- Human Interface Devices (HID): Includes keyboards, mice, and game controllers.
- Mass Storage: For external drives, flash storage, and media devices.
- Audio: Handles digital audio transfer for headsets, speakers, and audio interfaces.
- Communications and CDC Control: Used for networking devices such as modems.
Introduction to common USB protocols
Four main data transfer types exist within USB, each optimized for different tasks:
- Control Transfers: Used for device setup and configuration, including the initial enumeration process when a device is first connected.
- Bulk Transfers: Efficient data transfer protocol for large amounts of data (e.g., for external hard drives).
- Interrupt Transfers: Typically used for low-latency, time-sensitive data (e.g., for keyboards and mice).
- Isochronous Transfers: Reserved for data streams that require consistent timing, such as audio and video devices.
HID Protocol
Now that we’ve covered how USB works on a hardware level and its basic protocols, let’s dive into the specific protocol that makes communication with input devices like keyboards possible: the Human Interface Device (HID) Protocol.
General Overview of the HID Protocol
The Human Interface Device (HID) Protocol was created to standardize the way devices like keyboards, mice, and game controllers communicate with computers. It simplifies device-to-host communication by abstracting the details of low-level data transmission.
Definition and key use cases of HID
HID devices interact with the host by sending reports that describe user input (such as a keypress or mouse movement). This standardized communication allows for plug-and-play functionality, meaning devices work without requiring specific drivers.
The protocol is optimized for devices that require low-latency, small data transfers at regular intervals, including:
- Keyboards for keypresses,
- Mice for movement and button states,
- Joysticks and other input devices.
HID supports a broad range of consumer electronics and ensures a unified framework for input devices that handle user interactions.
Transaction Types and Data Flow in the HID Protocol
Communication in the HID protocol involves three main types of transactions: IN, OUT, and SETUP. Each transaction occurs between the device and the host, following a strict sequence to ensure the integrity and reliability of the data being transmitted.
IN, OUT, and SETUP Transactions
-
IN Transactions: These occur when the host requests data from the device. For example, when a keyboard sends a report of which keys are currently pressed, this data is sent in response to an IN transaction.
-
OUT Transactions: These are initiated by the host to send data to the device. In the case of HID, OUT transactions can be used to send commands or configurations, such as setting the status of indicator LEDs on a keyboard.
-
SETUP Transactions: These are used primarily during the enumeration process, where the host configures the device and requests information such as device descriptors, configuration descriptors, and HID-specific report descriptors.
Role of Endpoints
HID devices use Interrupt Endpoints to enable low-latency data transfer, ensuring data is sent and received at regular intervals. This setup is ideal for input devices like keyboards and mice, which require prompt response times.
Other Important Steps in HID Communication
In addition to the handshake, HID communication involves several critical steps that facilitate the proper operation of devices. These include the exchange of descriptors and the structured format of HID reports.
Descriptor Exchanges
Descriptors are fundamental in the HID protocol because they describe the device’s capabilities and how it will communicate with the host.
Device Descriptor: This descriptor provides basic information about the device, such as its vendor ID, product ID, and supported protocols.
Configuration Descriptor: Contains information about the power requirements and the number of interfaces the device supports. Each interface may have multiple endpoints and be dedicated to different functions.
Report Descriptor: This is specific to HID devices and outlines the format of the reports that will be sent between the device and the host. For example, in a keyboard, the report descriptor defines the structure for sending keypress data, including how many keys can be pressed simultaneously and how modifier keys (like Shift or Ctrl) are handled.
Report Format: Input, Output, and Feature Reports
HID devices use reports to exchange data with the host.
There are three main types of reports:
-
Input Reports: These are sent from the device to the host, typically carrying information like keypresses or mouse movements. For a keyboard, an input report might contain the key codes corresponding to the currently pressed keys.
-
Output Reports: These flow from the host to the device. Output reports are used for commands such as turning on the num lock LED on a keyboard.
-
Feature Reports: Feature reports are used for device-specific settings that are not time-sensitive. For instance, configuring a game controller’s sensitivity settings might be done through a feature report.
These reports ensure that the device and host can efficiently communicate both status updates and configuration commands.
HID Keyboard Case
In this section, we’ll apply key elements from the HID Protocol overview—such as report types, transaction flows, and descriptors—to the specific case of USB keyboards, focusing on how they transmit keypress data to a host.
The HID protocol is highly relevant to keyboards, which are among the most commonly used input devices. Keyboards use a specific subset of the HID protocol that simplifies the communication of keypresses and releases to the host system.
Specific Features and Handling for Keyboards
Keyboards must communicate keypresses and releases efficiently, including handling modifier keys like Shift, Ctrl, and Alt.
Key Press/Release Reporting
In HID keyboards, every key is associated with a key code. When a key is pressed, the keyboard sends an input report to the host, which includes the key code for the pressed key(s).
For example:
- A keyboard might send a report with the key code for the letter “H” when the “H” key is pressed.
- When the key is released, a report is sent with either no key code.
Keyboards typically support the simultaneous pressing of multiple keys, referred to as N-key rollover. In a basic setup, most keyboards can handle up to six simultaneous keypresses, while gaming or specialized keyboards can support more.
Modifier Keys (Shift, Ctrl, etc.)
Modifier keys, such as Shift, Ctrl, and Alt, play a unique role in the HID keyboard protocol. These keys don’t produce characters by themselves but modify the output of other keys. For instance, pressing Shift with the “A” key sends a report for an uppercase “A”.
In HID, modifier keys are handled by specific bits in the report descriptor. When a modifier key is pressed, the corresponding bit is set, and the host understands that any subsequent keypress should be modified (e.g., a capital letter or a special character).
Enumeration Process for Keyboards
The enumeration process begins when a keyboard is plugged in. This process involves the host requesting and receiving the device descriptor and report descriptor from the keyboard, setting up the communication pathway.
-
Device Descriptor: The host retrieves basic information about the keyboard, such as its vendor ID and product ID.
-
Report Descriptor: The host requests the report descriptor, which outlines how data will be sent and interpreted. This includes defining key codes and how modifier keys work.
-
Polling: Once enumeration is complete, the host periodically polls the keyboard’s interrupt endpoint to check for input reports.
Example of HID Report for Keyboards
In a typical input report for a keyboard:
- The first byte represents the status of the modifier keys (Shift, Ctrl, etc.).
- The second byte is reserved and not typically used.
- The third through eighth bytes contain the key codes for up to six simultaneously pressed keys. If fewer than six keys are pressed, the remaining bytes are filled with 0x00.
For example, if the Shift key and the “A” key are pressed together, the report might look like:
[ 0x02, 0x00, 0x04, 0x00, 0x00, 0x00, 0x00, 0x00 ]
Here:
- 0x02 indicates the Shift key is pressed.
- 0x04 represents the key code for the letter “A”.
Conclusion
In this article, we explored the USB architecture, including its protocols and device classes, to understand how communication with devices like keyboards is achieved. By examining the Human Interface Device (HID) protocol specifically, we saw how keyboards interact with a host system through structured data exchanges, enabling efficient and reliable input handling.
In Summary: We learned how USB and HID protocols facilitate keyboard communication with computers, from low-level signaling to specific keypress reporting. This knowledge gives insight into how everyday devices like keyboards work seamlessly with various systems, ensuring consistent performance across applications.