USB devices are everywhere in modern computing, from keyboards and mice to game controllers and specialized hardware. While most devices work out of the box thanks to generic drivers, understanding how they communicate with the operating system opens up possibilities for custom implementations, debugging, and learning about low-level hardware interaction.
This article explores the process of reverse engineering a USB device’s communication protocol and implementing a custom Linux kernel driver. We’ll focus on the Sony DualShock 4 controller as our target device, chosen for its widespread availability and relatively straightforward HID protocol implementation.
The goal is to understand how USB HID devices communicate, capture and analyze their data packets, and finally write a minimal Linux kernel driver that can read input from the controller. This knowledge is transferable to other USB devices and provides insight into how operating systems interact with hardware at a low level.
Understanding USB HID Devices
What is HID?
The Human Interface Device (HID) protocol is a USB standard designed for devices that interact directly with humans, such as keyboards, mice, joysticks, and game controllers. HID devices use a standardized way of describing their capabilities and communicating with the host system, making them relatively easy to work with once you understand the fundamentals.
Key USB Concepts
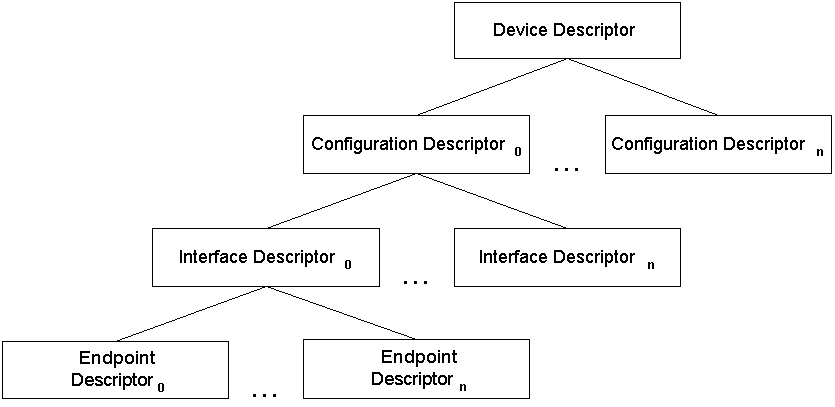
Before diving into reverse engineering, it’s important to understand some basic USB terminology:
-
Endpoints are communication channels between the host and device. Each endpoint has a direction (IN for device-to-host, OUT for host-to-device) and a type (control, interrupt, bulk, or isochronous). HID devices typically use interrupt endpoints for real-time data like button presses.
-
Interfaces represent different functions or modes of a device. A single USB device can have multiple interfaces - for example, a gaming headset might have separate interfaces for audio and microphone functionality.
-
Descriptors are data structures that describe the device’s capabilities and configuration. The device descriptor contains basic information like vendor ID (VID) and product ID (PID), while HID descriptors specify the format of input and output reports.
USB HID Communication Model
HID devices communicate using reports - structured data packets that contain input from the device (like button states) or output to the device (like LED control). These reports follow a format defined by the device’s HID descriptor, which acts as a template for interpreting the raw data.
The DualShock 4 controller, like most game controllers, primarily sends input reports containing button states, analog stick positions, and sensor data. Understanding this report structure is crucial for writing a driver that can interpret the controller’s data.
For a deeper understanding of the HID protocol, see this article.
Reverse Engineering the Protocol
Setting Up the Environment
You can list connected USB devices using:
|
|
This shows the DualShock 4’s vendor ID (054c) and product ID (09cc), which we’ll need later for the driver.
Capturing USB Traffic
Enable USB monitoring by loading the usbmon kernel module:
|
|
usbmon is a kernel module that allows monitoring USB traffic in real-time. You can use it directly or with Wireshark to visualize packets.
For HID devices, you can also view raw data directly:
|
|
Identifying the Correct /dev/hidraw* Device
If you have multiple HID devices, you can identify which /dev/hidrawX corresponds to your controller:
|
|
Compare the idVendor and idProduct values with the ones from lsusb (054c:09cc). The matching device is your DualShock 4.
Device-Specific Case Study: DualShock 4
Although we often refer to them as analog controls, the stick and trigger readings are already digitized — they’re discrete 8-bit integers (0–255) representing positions.
| Control | Byte Index | Center Value | Notes |
|---|---|---|---|
| Left Stick X | 1 | 0x80 (128) |
Horizontal |
| Left Stick Y | 2 | 0x80 (128) |
Vertical |
| Right Stick X | 3 | 0x80 (128) |
Horizontal |
| Right Stick Y | 4 | 0x80 (128) |
Vertical |
Writing a Minimal Linux Kernel Driver
The Linux USB API
The Linux kernel provides an API for USB driver developers, including:
- Device registration:
usb_register_driver()andusb_deregister() - Device matching: via
usb_device_idtables - Data transfer:
usb_control_msg(),usb_bulk_msg(), andusb_fill_int_urb() - Memory management:
usb_alloc_urb(),usb_free_urb(), andusb_alloc_coherent()
These functions form the foundation for writing USB drivers in Linux.
Understanding URBs (USB Request Blocks)
URBs (USB Request Blocks) are data structures representing asynchronous USB transactions. Each URB includes a buffer, endpoint, transfer length, and a callback function that is triggered when the transfer completes.
Kernel Module Structure
Below is a simplified example of a USB driver initialization:
|
|
Implementing the Probe Function
The probe function is called when a matching device is connected. It’s responsible for setting up the driver’s internal state and configuring communication with the device:
|
|
Handling Input Data
USB communication in kernel drivers uses URBs (USB Request Blocks). For interrupt endpoints like those used by HID devices, you set up a URB with a callback function that gets called whenever data arrives:
|
|
Creating a Device Interface
For user-space applications to access the driver, you can create a character device or use existing interfaces like the input subsystem. A simple approach is creating a device file that applications can read:
|
|
Building and Loading the Module
Compile the driver using a Makefile that specifies the kernel build system:
|
|
Load the module with sudo insmod ds4_driver.ko and check dmesg for output when you use the controller.
Info
if when when executing dmesg and you don’t see any output related to your driver, make sure you controller isn’t binded to another driver, you can check this by running lsusb -vt and looking for the correct bus and port numbers which usually look like this bus.port.port:config.interface.
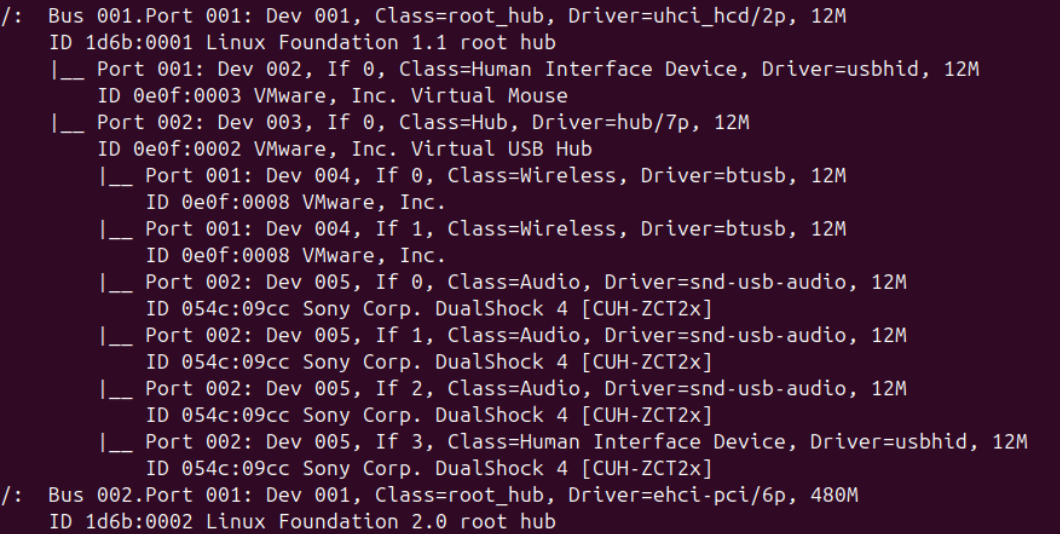
In our case, it is 1.2.2:1.3, to be really sure you can also run ls /sys/bus/usb/devices/usbhid/ and check if the device is listed there.
Then finally, you can unbind the device from the usbhid driver by running:
|
|
and rebind it to your driver by running:
|
|
Error Handling and Cleanup
Proper error handling is crucial in kernel code. Always check return values and clean up resources on failure:
|
|
You can find a minimal implementation of the driver on github.
Conclusion
Reverse engineering USB devices like the DualShock 4 controller provides valuable insights into low-level hardware communication. By understanding the HID protocol, capturing USB traffic, and implementing a custom Linux kernel driver, you gain practical experience in systems programming and device interaction.
Key takeaways:
- Understanding USB HID protocols and descriptors is essential for interpreting device data.
- Tools like
lsusb,usbmon, and Wireshark are invaluable for capturing and analyzing USB traffic. - Writing a Linux kernel driver involves setting up device registration, handling URBs, and managing memory and resources carefully.
- Testing and debugging kernel code requires careful attention to error handling and cleanup.
This process not only enhances your debugging skills but also opens up possibilities for creating custom applications and drivers for various USB devices. The techniques demonstrated here can be applied to other HID devices, making it a versatile skill set for any aspiring systems programmer or hardware enthusiast.
As you continue exploring USB devices, consider experimenting with different controllers or peripherals to deepen your understanding of USB protocols and driver development. The skills learned here are foundational for anyone interested in systems programming, embedded systems, or hardware hacking.