0. Prerequisites
If you’re new to side-channel attacks, watching this video by Ledger and reading this article by Jake Hertz will make your reading experience smoother.
1. Introduction
YubiKeys are hardware-based security tokens widely used for two-factor authentication, providing users with a highly secure, physical method of accessing systems and accounts. Developed by Yubico, these devices have become staples in professional environments, safeguarding sensitive data against digital threats.
However, EUCLEAK, a recent breakthrough from the security research team at NinjaLab, has exposed a significant vulnerability in YubiKey’s cryptographic library. EUCLEAK revealed that the YubiKey 5 Series is susceptible to side-channel attacks that can expose private keys, rendering these otherwise secure devices vulnerable. Through detailed reverse-engineering, NinjaLab demonstrated that, by measuring variations in the device emissions during cryptographic processes, attackers could potentially extract YubiKey private keys.
This discovery is concerning due to both YubiKey’s widespread use and the age of the flaw, the vulnerability has gone undetected for over 14 years. EUCLEAK underscores the critical need for rigorous security evaluations in trusted hardware to protect against evolving side-channel and hardware attack techniques.
2. Electromagnetic Side-Channel Attacks: Capturing Secrets Through EM Waves
What makes EM attacks unique ?
Electromagnetic (EM) side-channel attacks are a special type of side-channel attack, it allows a person to capture the EM radiation that devices emit while performing operations.
Cryptographic devices, like YubiKey, process large amounts of data through complex mathematical operations, generating EM signals as a by-product of these computations. These signals contain clues about what’s happening inside the device, like which data is being processed or which operation is being computed.
The time it takes to perform these operations, alongside the corresponding EM emissions, can reveal parts of the data being processed, such as the private key or random nonce used in signature generation.
What makes EM attacks especially powerful is their ability to extract sensitive information without having to breach the device’s software or encryption directly. Instead, attackers analyse the patterns in EM emissions to infer the internal state of the device during cryptographic operations. Even the slightest variations in how long a certain cryptographic operation takes can be enough to reveal useful information. In fact, we’re dealing with nanoseconds precision for such computation.
Here’s a diagram demonstrating how a standard EM side-channel attack operates:
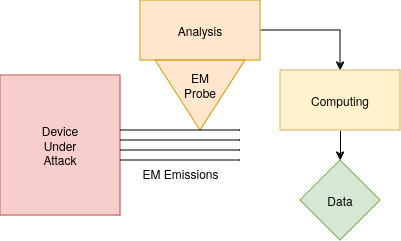
Why EM emissions are dangerous for cryptographic devices
The YubiKey, like many other secure devices, was not designed with EM emissions as a significant security risk. However, during cryptographic operations the device unintentionally emits small EM signals. These signals are typically weak and may seem like harmless noise, but they carry valuable information about the cryptographic process being performed.
The danger lies in the fact that even small variations in the timing or intensity of these EM signals can reveal sensitive data, such as private keys or other secret values. Devices that don’t account for these physical emissions leave themselves vulnerable to side-channel attacks. The attackers can exploit this unintended leakage to reconstruct confidential information without needing to directly breach the device’s encryption or software. In the case of YubiKey, this unintentional data leakage through EM emissions was precisely what made it susceptible to exploitation in the EUCLEAK attack.
3. The Vulnerability in YubiKey’s ECDSA: How Non-Constant Time behaviour Was Exploited
How the ECDSA Algorithm Works
The Elliptic Curve Digital Signature Algorithm (ECDSA) is widely used in cryptographic devices like YubiKey to generate digital signatures, providing authentication without revealing sensitive information like the private key. At the heart of ECDSA is the modular inversion process, which is part of the signature generation step.
Here’s a brief overview of how ECDSA works in the context of signature generation:
- A private key and an elliptic curve point (public key) are used to generate a signature on a message.
- A random nonce
kis generated for each signature, ensuring that even if the same message is signed multiple times, the signatures remain different. - The crucial step in this process is computing the modular inverse of the nonce
k. This step must be done with caution, as any leakages from this computation can compromise the private key.
The security of ECDSA relies heavily on the fact that the nonce k used during signature generation is random and remains secret.
If an attacker can recover the nonce k, they can use it to extract the private key.
This is where constant time execution becomes essential.
constant time algorithms are designed to ensure that the execution time of critical operations does not vary based on the values being processed.
If the time it takes to execute the modular inversion differs depending on the input values (in this case, the nonce k), attackers can use these timing variations to gain insights into the nonce itself.
The Discovery of Non-Constant Time behaviour in Infineon’s ECDSA Implementation
NinjaLab suspected that there was a flaw in Infineon’s implementation of ECDSA in the YubiKey 5, precisely in the modular inversion step.
Theirs hypothesis was that this function was implemented in a non-constant time fashion and that it could leak the nonce k.
If an attacker could observe how long the modular inversion takes over multiple signatures, they could correlate these timing variations with specific values of k and use this information to extract the private key.
By targeting this step, NinjaLab realized that the modular inversion was the perfect entry point for an EM side-channel attack. They suspected that timing variations during this step could be captured through EM emissions, providing a window into the cryptographic process.
4. Reverse Engineering YubiKey’s Cryptographic Library: Cracking the Code
To successfully exploit the vulnerability found in YubiKey 5 Series and extract the private key, NinjaLab needed to understand the exact behaviour of the cryptographic algorithms inside the secure element of the device. This required a deep dive into the cryptographic library used by the YubiKey, particularly the Extended Euclidean Algorithm (EEA) used in modular inversion during ECDSA signature generation.
Leveraging JavaCard for Early Insights
Before directly attacking the YubiKey, NinjaLab needed a platform where they could freely experiment and study the behaviour of modular inversion in ECDSA. To do this, they turned to the Feitian A22 JavaCard but why this specific card ? Because of four main points:
- The JavaCard allowed NinjaLab to run experiments in a controlled environment, where they could manipulate the cryptographic inputs, measure timing behaviour, and observe how the cryptographic library performed operations.
- This open platform helped them understand the critical modular inversion process in ECDSA and identify potential weaknesses in the algorithm’s implementation.
- It’s a platform that shares similarities with YubiKey’s hardware such as the use of the Infineon SLE78 cryptographic library.
- On the JavaCard, they could generate signatures using known private keys and nonces, allowing them to measure the timing of the modular inversion operation and confirm whether it was running in constant time or not.
By working with the JavaCard, NinjaLab was able to map out how the modular inversion step was handled in the ECDSA signature process. They realized that their hypothesis was right, the non-constant time execution of the modular inversion step can create an exploitable weakness, which they could later target using EM side-channel analysis.
Reverse Engineering Infineon’s Extended Euclidean Algorithm
Once NinjaLab had gathered enough information from their experiments with the JavaCard, they shifted their focus to reverse engineering the EEA used in the YubiKey’s cryptographic library. This step was crucial to understanding the non-constant time behaviour that would ultimately allow them to extract the private key.
The EEA is a mathematical process used to compute the modular inverse of a number, a crucial step in the ECDSA signature generation.
In cryptographic terms, the modular inversion is used to compute s = k⁻¹ * (h + r * d) mod n, where k is the nonce, h is the hash of the message, r is a part of the signature, and d is the private key.
Through reverse engineering, NinjaLab discovered that the EEA implementation in the YubiKey’s cryptographic library had a critical flaw: the time it took to complete the modular inversion varied depending on the bit-length of the values being processed.
The algorithm had branches that performed different numbers of iterations depending on the size of the nonce k.
Each step in the inversion process either reduced the size of k or continued processing it, leading to timing variations that leaked valuable information about the nonce.
This non-constant time behaviour was the root cause of the vulnerability.
It meant that the amount of time required to compute the modular inverse could reveal the size and value of the nonce k. By measuring these timing differences, NinjaLab could infer the private key with enough precision.
Confirming the Attack: Real-World Key Recovery
Once NinjaLab confirmed the timing vulnerability in the YubiKey’s ECDSA signature generation, they moved to demonstrate a complete key recovery in real-world conditions.
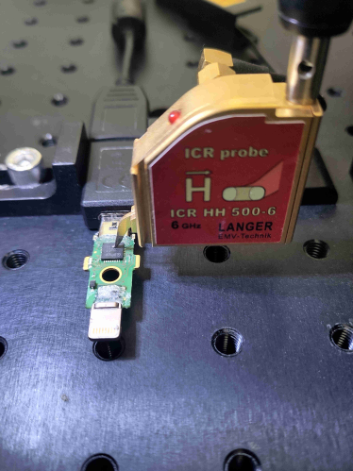

By repeating the signature generation process multiple times and capturing extensive sets of EM traces, they reconstructed the cryptographic operations step-by-step.
NinjaLab’s final breakthrough came when they successfully derived the private key.
Through careful analysis of the captured EM signals, they were able to pinpoint the timing differences for each iteration of the EEA during the modular inversion step.
Over time, these differences revealed enough information to fully recover the nonce k, and by extension, the private key.
This result marked a significant achievement: NinjaLab had proven that the non-constant time behaviour in YubiKey’s cryptographic library was not just theoretical but could be exploited under real-world conditions. The ability to recover the private key confirmed the critical flaw in the ECDSA implementation, showcasing the risk posed by side-channel attacks on the YubiKey 5 Series.
5. Why It Stayed Hidden for 14 Years: The Overlooked Vulnerability
Despite the YubiKey’s strong reputation and widespread use in securing everything from personal accounts to high-level corporate systems, the flaw persisted across multiple product generations.
How Did This Go Undetected?
The Infineon cryptographic chips used in YubiKey devices are widely trusted, largely because they undergo multiple certifications, such as the Common Criteria (CC). These certifications make sure that security products meet expectations, particularly in terms of functionality and resistance to known attack methods.
The CC certification process focuses on ensuring that devices perform functionally as expected. This means that cryptographic algorithms, like ECDSA, are evaluated based on their correctness.
However, these certifications do not prioritize side-channel attack resilience. Functional correctness doesn’t account for timing variations or physical emissions like EM radiation, which can leak information even when the cryptographic algorithm is functionally correct. At the time this flaw was introduced, 14 years ago, side-channel attacks were considered theoretical or less practical.
In the mid-2000s, when this vulnerability first appeared, the emphasis in security evaluations was placed on logical attacks, where attackers try to exploit flaws in the software or algorithm design. The physical aspects of devices, such as timing differences or EM emissions, were considered harder to exploit and required sophisticated setups, so they weren’t prioritized in evaluations.
Side-channel attacks were still in their early stages. While theoretically possible, the consensus at the time was that such attacks would be difficult to carry out in real-world scenarios. As a result, the non-constant time execution of the EEA used in Infineon’s ECDSA implementation didn’t raise alarms when it was first certified.
Infineon’s cryptographic library passed through several generations of products and certifications without focus on its resistance to physical, side-channel attacks. The reliance on traditional certification standards allowed this vulnerability to slip through undetected, even as side-channel attacks became frequent.
Challenges in Detecting EM-Based Attacks
Even if side-channel testing had been part of the evaluation process, detecting an EM-based attack like the one used in EUCLEAK is still challenging. Several factors make it difficult to identify and exploit EM vulnerabilities, which is why this flaw persisted for so long.
One of the biggest challenges in detecting and exploiting side-channel vulnerabilities is the need for physical access to the device. Unlike traditional cyberattacks, which can be carried out remotely through software or network vulnerabilities, an EM-based attack requires the attacker to be physically close to the device to capture emissions.
Capturing and analyzing EM emissions from cryptographic operations isn’t something that can be done easily or cheaply, it requires precise EM probes, oscilloscopes, and sophisticated signal processing techniques to filter out noise and identify timing variations.
At the time the vulnerability was first introduced, the cost and complexity of performing such an attack were barriers that made side-channel vulnerabilities seem less urgent. The expensive and complex setup needed to carry out the attack contributed to why it was overlooked during security evaluations. Even now, the setup used by NinjaLab for the EUCLEAK attack cost more than 10 thousands euros.
Beyond the technical challenges, side-channel attacks also require specialized knowledge in hardware security, EM theory, and cryptographic analysis. This niche expertise limited the number of people capable of both discovering and exploiting such vulnerabilities.
Implications for Cryptographic Devices
The most surprising aspect of the EUCLEAK vulnerability is its longevity. It persisted across multiple generations of Infineon’s secure elements, including those used in YubiKey and other products like the Optiga Trust M and Optiga TPM modules. This long lifespan points to a broader issue in the way cryptographic devices are evaluated and certified.
Cryptographic chips, once designed and certified, often have a long lifecycle and are used in various products for many years. If a vulnerability goes undetected in the initial stages, it can easily propagate through different product lines.
The EUCLEAK attack highlights the need for a shift in the way cryptographic devices are evaluated, particularly when it comes to hardware attacks. As these attacks become more feasible with cheaper equipment and more accessible knowledge, cryptographic devices need to be tested for real-world threats, not just functional correctness. This requires a broader approach to testing that includes simulated real-world scenarios where physical access and advanced equipment are part of the attack model.
Furthermore, cryptographic hardware is constantly exposed to new attack techniques as research evolves. Companies need to adopt an ongoing approach to security testing, regularly re-evaluating their products against emerging threats and updating them accordingly.
6. Patching the Vulnerability: From Discovery to Security Updates
Infineon and Yubico’s Response
After NinjaLab’s discovery of the EUCLEAK vulnerability in the YubiKey 5 Series, Infineon and Yubico quickly took action to address the critical flaw. While this vulnerability had gone unnoticed for over 14 years, the rapid response following its revelation was crucial in preventing further exploitation.
Recognizing the severity of the attack, they released a series of updates aimed at patching the vulnerability and ensuring that future attacks would be nullified.
One of the significant steps taken by Yubico was the release of firmware update 5.7 for the YubiKey 5 Series. This update ensured that the modular inversion process in ECDSA now runs in constant time which effectively closes the timing side-channel that was exploited.
Alongside constant time execution, other optimizations were made to improve the overall security of the cryptographic operations in YubiKey, including blinding techniques to defend against side-channel leaks.
The discovery of the EUCLEAK vulnerability was handled through a coordinated disclosure process between NinjaLab, Infineon, and Yubico.
Responsible disclosure allowed these companies to release security patches before the vulnerability could be widely exploited by malicious actors. Thanks to this quick response and collaboration, Infineon and Yubico were able to minimize the impact of the vulnerability, releasing fixes before widespread exploitation became a significant threat.
Countermeasures Against EM Attacks
As side-channel attacks like EUCLEAK become more feasible and accessible, cryptographic devices need to implement robust countermeasures to prevent attackers from extracting sensitive information via EM emissions and timing variations.
The EUCLEAK patch incorporated several key defences that are now essential in protecting against side-channel attacks.
One of the most effective countermeasures against timing attacks, including EM-based side-channel attacks, is the implementation of constant time algorithms. These algorithms are designed to ensure that all operations take the same amount of time, regardless of the input values being processed. In a constant time algorithm, the execution time is independent of the input data. This means that attackers observing the timing of operations cannot give any useful information about the cryptographic inputs, making timing-based attacks much harder, if not impossible.
Blinding is another critical defence mechanism used in modern cryptographic implementations to prevent side-channel attacks.
In the context of ECDSA, blinding involves adding a random value to the cryptographic operation to mask the real values being used, making it harder for attackers to correlate side-channel emissions with the actual data.
In the modular inversion process, a random blinding factor is introduced to mask the real value of the nonce k.
This ensures that even if an attacker captures EM emissions during the inversion, they cannot easily correlate those emissions with the actual value of k or the private key.
The combination of blinding techniques and constant time execution is a powerful defence against side-channel attacks. While constant time algorithms prevent timing variations, blinding adds another layer of obfuscation, making it significantly more challenging for attackers to extract meaningful information from side-channel traces.
While constant time algorithms and blinding techniques address the cryptographic side of the vulnerability, physical defences can also help protect devices from EM side-channel attacks. Some modern cryptographic devices now incorporate EM shielding to reduce the amount of EM radiation emitted during cryptographic operations. This can make it more difficult for attackers to capture clear EM signals, adding layers of defence against side-channel attacks. In addition to EM shielding, some devices use physical isolation techniques that prevent attackers from getting close enough to capture EM signals. This is particularly important in environments where devices like YubiKey are used in high-security contexts.
Improving Future Certifications and Testing
The EUCLEAK vulnerability and its subsequent patching underscore the need for a change in how cryptographic devices are evaluated and certified.
As side-channel attacks become cheaper and more practical, the industry must adapt its security testing and certification standards to account for these evolving threats. Historically, security certifications like the CC have focused primarily on functional correctness and resistance to logical attacks.
However, the EUCLEAK attack has shown that side-channel vulnerabilities can persist even in devices that pass these security evaluations. Future certifications must include testing for side-channel vulnerabilities, particularly those involving timing analysis and EM emissions. This means evaluating devices for their ability to resist side-channel attacks, whether through constant time implementations, blinding, or physical defences like EM shielding. Cryptographic devices should be tested not only in controlled laboratory environments but also in real-world scenarios that mimic practical attack conditions. This includes testing the resilience of devices to physical side-channel attacks, where attackers have physical access to the device and can capture EM emissions or timing data.
As the cost of specialized equipment like EM probes and oscilloscopes decreases, and as more research is published on side-channel attack techniques, these attacks are no longer restricted to state-sponsored actors or highly specialized labs. What was once considered an “advanced attack” requiring expensive tools and expert knowledge is now within reach of independent researchers and well-funded attackers. The growing availability of resources and tools for performing side-channel attacks means that cryptographic devices must be designed and tested with these evolving threats in mind. As these attacks become cheaper and more accessible, they will also become more dangerous. Companies developing cryptographic devices, like Yubico, must remain vigilant and proactive, ensuring that their devices are protected against both current and future threats.
7. Conclusion: The Long-Term Impact of EUCLEAK on Cryptographic Security
The discovery of EUCLEAK by NinjaLab revealed a critical vulnerability in the YubiKey 5 Series that had gone undetected for 14 years. By exploiting EM side-channel attacks, NinjaLab was able to expose weaknesses in the ECDSA implementation, specifically the non-constant time execution of the modular inversion step. This allowed them to extract the private key, a severe security breach for such a widely trusted device. The flaw was tied to Infineon’s cryptographic library, and its existence across multiple products highlights the dangers of overlooking side-channel vulnerabilities in security evaluations.
Going Further
The implications of EUCLEAK extend beyond just YubiKey. The same cryptographic library is used in many other devices built with Infineon’s secure elements, including e-passports, TPM modules, and IoT devices. This means that a broad range of industries, including finance, government, and consumer electronics, are potentially exposed to similar risks. The vulnerability sheds light on the need for stronger hardware security in cryptographic systems, particularly in how they defend against side-channel attacks. Moving forward, it is critical that certification processes for secure elements include real-world testing that accounts for physical attack vectors like EM emissions, ensuring that cryptographic devices are equipped to resist emerging threats.
Sources
Original Paper on the EUCLEAK attack by NinjaLab : https://ninjalab.io/wp-content/uploads/2024/09/20240903_eucleak.pdf
Yubico security advisory for the EUCLEAK attack : https://www.yubico.com/support/security-advisories/ysa-2024-03/
side-channel attack with basic radio equipment : https://www.cosade.org/cosade19/cosade15/proceedings/paper_S10_2.pdf
Article on EM attacks : https://www.allaboutcircuits.com/technical-articles/em-side-channel-attacks-on-cryptography/
Article on ECDSA : https://www.allaboutcircuits.com/technical-articles/elliptic-curve-cryptography-in-embedded-systems/
EM prevention : https://www.allaboutcircuits.com/technical-articles/a-primer-on-side-channel-attack-countermeasures-and-prevention/
Artcile on EM shielding : https://www.strouse.com/blog/what-is-emi-shielding
Infineon chips on passports : https://www.securetechalliance.org/infineon-ships-security-chips-to-taiwans-electronic-passport-program/